EIGRP, backup and default gateway
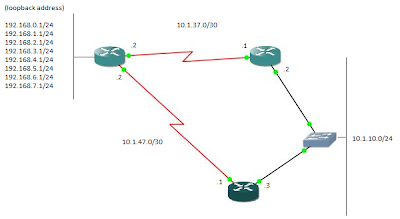
EIGRP configuration go to cyb n png, type this command on both router Cyb(config)#router eigrp 1 Cyb(config-router)#network 10.0.0.0 Cyb(config-router)#no auto-summary # router eigrp 1 : You can choose any number for eigrp from 1-65535, router with the same eigrp AS number will exchange routing information each others. # network 10.0.0.0 : all the interface with this address will be advertised to all router with eigrp 1 #no auto-summary : if you are using classless IP address in your network, this command should be apply, if not, router gonna summarize all the network and only advertise it as a single network. It may cause looping problem. Classfull network not gonna effected After eigrp is set on the 2 nd router, you’ll notice there’s a message as picture above, this mean that both router are learning each other, they both advertise the network 10.x.x.x as defined in the command. Type #show ip eigrp interface to know which interface is advertise, in this case, ...

